Do you love solving puzzles? Do you enjoy researching how things work — especially technology and computing systems? Or even better: do you drag your friends to escape rooms? If you answer yes to any of these questions, a career in ethical hacking might be for you.
Ethical hacking is all about finding weaknesses in computer systems and networks and fixing them. Some ethical hackers work for small companies, completing quality assurance and penetration testing. Other ethical hackers work for tremendously large enterprises—hacking banks, government entities, and other highly-secured organizations.
A great place to start your ethical hacking career is through ethical hacking courses. However, there are other avenues. Keep reading to learn how to become an ethical hacker!
What is Ethical Hacking?
Ethical hacking means using hacking techniques to test the computer system or network’s security. Ethical hackers search for ways to break into a system to find security vulnerabilities that malicious hackers could exploit. Ethical hacking is also known as penetration, white hat, or security testing.
Unlike malicious hackers, ethical hackers don’t attempt to gain unauthorized access to systems or data. Instead, they aim to help organizations improve security by searching and fixing potential security risks. Ethical hacking tests the security of any computer system, from individual networks to large-scale enterprise systems.
Ethical hackers use several tools and techniques to find security vulnerabilities, including port scanning, web application attacks, and database attacks. By finding and fixing these vulnerabilities before they can be exploited, ethical hackers can help organizations strengthen their defenses against malicious attacks.
Upskill Yourself With Live Training
Role of Ethical Hacker
Knowing who they are is vital before understanding how to become an ethical hacker in India. Ethical hackers, also called as white hat hackers, use hacking skills to find security vulnerabilities in computer systems and networks. They then work with the systems owners to find ways to fix the vulnerabilities before malicious hackers can exploit them.
So, what do they do? Many ethical hackers work as consultants, providing expertise to companies that need to shore up their cybersecurity. Other ethical hackers work for government agencies or in the private sector. Ethical hackers use the same strategies and tools as malicious hackers but do so with permission from the system owners they are testing.
Ethical hacking aims to help organizations improve security by identifying and addressing weaknesses before they can be exploited. They may also be hired to conduct social engineering tests, assessing an organization’s ability to defend against phishing and other attacks that rely on human interaction.
Also read: Cyber Security vs Data Science: Which is Better for Career in 2025?
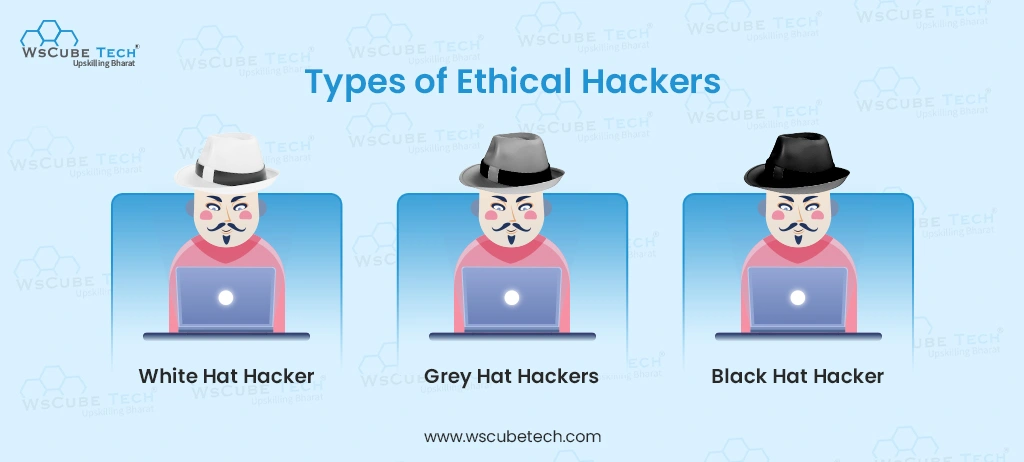
Types of Ethical Hackers
A hacker solves a technical issue using a computer, networking, or other abilities. Anyone using their skills to gain access to a system or network in an application to break laws is a hacker.
1. White Hat Hacker
White hat hackers, or ethical hackers, are cybersecurity experts assisting the government and businesses by performing penetration testing and identifying security flaws. Ethical hackers use various techniques to protect themselves from black hat hackers and other cybercriminals. They break into our system intending to find vulnerabilities and assist you in removing viruses and malware.
2. Black Hat Hacker
The main perpetrator of cybercrime, the crime agenda of a black hat hacker, is monetary. These hackers look for flaws in individual computers in banking systems and businesses. They can hack into the network and access personal, business, and financial details by exploiting loopholes.
3. Grey Hat Hackers
Grey hat hackers falls in between white and black hat hackers. They may not use their skills for personal gain but can have good and bad intentions.
For example, a hacker who hacks into an organization and comes across some vulnerability may leak it over the internet or inform about it to the organization. Hackers become black hat hackers when they use their hacking skills for personal gain.
Types of Cyber Attacks
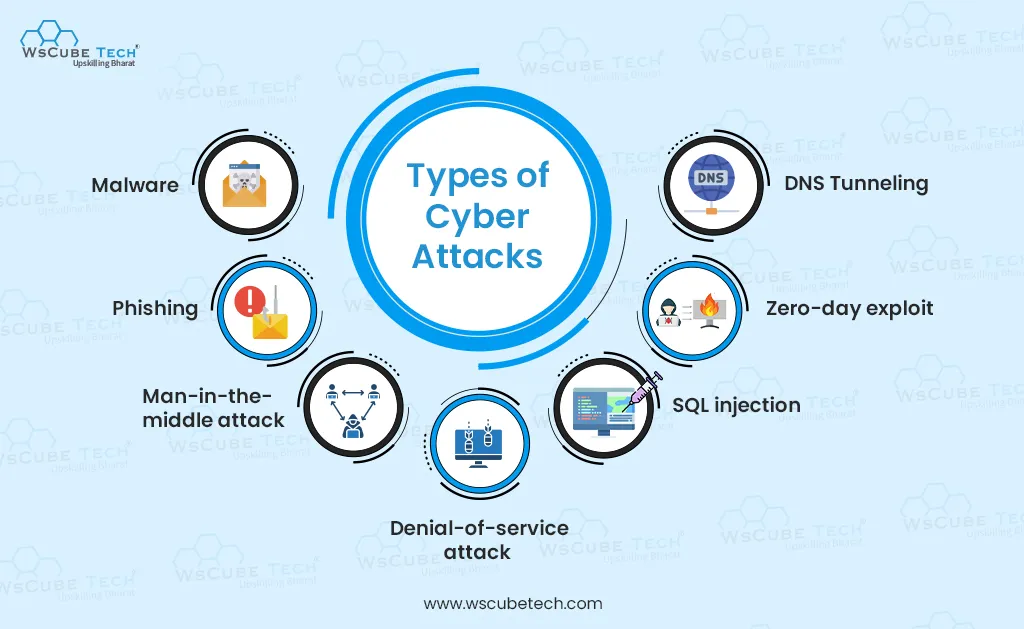
1. Malware
Malware describes malicious software that includes spyware, ransomware, viruses, and worms. It breaches a network through a vulnerability when an end user clicks a dangerous link or email attachment that installs risky software. Once inside the system, malware does the following:
- Blocks access to major components of the network
- Covertly obtains details by transmitting data from the hard drive (spyware)
- Installs malware or additional harmful software
- Disrupts particular components and renders the system inoperable
2. Phishing
Phishing sends fraudulent communications that appear to come from a reputable source, basically through email. This is to steal sensitive information like credit card and login details or to install malware on the victim’s machine. Phishing is an increasingly common cyber threat.
3. Man-in-the-middle attack
Man-in-the-middle (MitM) attacks, or eavesdropping attacks, occur when hackers insert themselves into a two-party transaction. Once the attackers interrupt the traffic, they filter and steal information.
Two common entry points for MitM attacks:
- Hackers insert themselves between visitors’ devices and networks on insecure public Wi-Fi. Unknowingly, the user passes all information through the hacker
- Once malware has breached a system, an attacker installs software to process the victim’s data.
4. Denial-of-service attack
This attack floods servers, networks, or systems, with traffic exhausting resources and bandwidth, making the system unable to fulfill legitimate requests. Also, attackers use multiple compromised devices to launch this attack, known as a distributed denial-of-service (DDoS) attack.
5. SQL injection
Here, a hacker inserts malicious code into a server using SQL and forces the server to reveal information it usually would not. An attacker performs this attack by submitting malicious code into a vulnerable website’s search box.
6. Zero-day exploit
A zero-day exploit attack hits before a network vulnerability is announced before a solution is implemented. Attackers target the disclosed vulnerability during this time. This vulnerability threat detection needs continuous awareness.
7. DNS Tunneling
This utilizes the DNS protocol to communicate non-DNS traffic over port 53 and sends HTTP and other protocol traffic over DNS. They disguise outbound traffic as DNS, concealing information shared through an internet connection.
DNS requests are manipulated to exfiltrate information from a compromised system to the attacker’s infrastructure for malicious use. Also, it can be used for command and control callbacks from the hacker’s infrastructure to a compromised system.
Interview Questions for You to Prepare for Jobs
Why to Choose Ethical Hacking for Career?
In today’s technology-driven world, cybersecurity has become a paramount concern for businesses and individuals. As the digital landscape expands, so does the need for skilled professionals who can safeguard information systems from malicious attacks.
Some reasons to have a career in ethical hacking include the following –
- Increased demands for information security professionals in both public and private sectors paving the way for more employment opportunities
- This field has extended beyond the digital world and is entering the physical world, thereby ensuring a real-world impact
- Booming job market, where pursuing an online Ethical Hacking course may help you get a better hike
- Opportunity to work with big brand names
- Fantastic opportunity to network with new people and industry experts.
Also read: How to Become Data Analyst? Skills, Qualifications, Full Roadmap 2025
Ethical Hacking Roadmap for Beginners
Let us learn how to be an ethical hacker in India.
1. Knowledge of computer systems and networks
Understand the functioning of computer systems, network protocols, operating systems, and how various components interact within a networked environment.
2. Proficiency in Programming Languages
Gain expertise in programming languages like:
- Python
- C++
- Java
- Java Script
- SQL
- Perl
- Ruby
3. Networking and Security Concepts
Familiarize yourself with the principles of computer networking, network security, and different security protocols. Understand how data is transmitted, secured, and protected in a networked environment.
4. Web Application and Database Knowledge
Develop an understanding of web application architectures, protocols, and database systems. Learn about common vulnerabilities specific to web applications such as :
- SQL Injection
- Cross-site scripting(XSS)
- Cross-site request forgery(CSRF)
5. Understanding of Operating Systems
Develop expertise in different operating systems like Windows, Linux, or macOS. This includes understanding system configurations, permissions, and security mechanisms specific to each operating system.
6. Familiarity with Ethical hacking Tools
Gain experience and knowledge with popular ethical hacking tools like:
- Metasploit
- Wireshark
- Nmap
- Burp Suite
- Kali
- Canavas
- SQL Ninja
- Wapiti
7. Problem-solving and Analytical Thinking
Ethical hackers must possess strong problem-solving skills and the ability to think analytically. You should be able to analyze complex systems, identify vulnerabilities, and devise effective strategies to mitigate potential risks.
8. Knowledge of Common Attack Vectors and Techniques
Understand various hacking techniques and attack vectors used by malicious hackers, such as social engineering, phishing, password cracking, or network-based attacks. This knowledge helps you anticipate and prevent potential threats.
9. Certifications
Certifications and skills will provide you with a great learning path. Also, these certificates describe your understanding of hacking techniques. You can get certified with an online ethical hacking course.
Also read: Python Developer Salary in India 2025 (Freshers & Experienced)
Tips to Become an Ethical Hacker
Along with the formal education, students can follow the below-mentioned steps to become an exceptional Ethical Hacker:
- Learn programming languages, tools, and operating systems such as C, Kali Linux, Python, etc.
- Master the art of having an anonymous presence online.
- Build a thorough knowledge of the networking concept.
- Explore and understand the hidden web.
- Comprehend and ace the skill of cryptography.
- Exploit the vulnerabilities, loopholes, and countermeasures of systems and networks to practice and gain experience.
- Conduct a case study to understand a cyber attack’s tactics, techniques, procedures, and scope.
- Update yourself with the latest technologies, software, and cyber security trends.

Eligibility to Become an Ethical Hacker
Here are the qualifications required for an Ethical Hacker.
Educational Qualification:
- Students must complete 10+2 or equivalent from a recognized board.
- They must secure a minimum aggregate score of 50% in their 10+2.
- Candidates must also appear in the concerned entrance exam and match the cut-off to secure admissions.
Required Skills
Here are the top skills required to be an ethical hacker:
- Programming
- Security analysis
- Research ability
- Systemization
- Effective problem-solving skills
- Analytical and rational thinking
- Observational skills
- Agile and spontaneous
- Practical approach
Career in Ethical Hacking
There needs to be more than knowing how to become an ethical hacker for the candidates who want to become hackers. It would help if you had an idea of the career and life of a hacker, as it’s filled with excitement working in several organizations.
Their advanced technology skills are to penetrate and locate any theft or illegal cyber activities with proper authorization. Moreover, ethical hackers serve the government and private organizations for national and international security.
Considering jobs in hacking, a qualified candidate will find opportunities in the following:
- Security Consultants
- Security Auditors
- Network Architects
- System Analysts
- Technical Support Engineers
- Security Administrators
Demand for Ethical Hackers in 2025
Amid the ongoing wave of cybercrime, the demand for cybersecurity experts, in general, and ethical hackers is high. With the immense globalization and the companies expanding their business, all companies need to have their data safe and secure.
These are the areas where ethical hackers are required to keep the company’s data safe and avoid any cyber attack. IT firms are the prominent recruiters. Nowadays, every company is expanding their business and going online. They recruit ethical hackers or cyber experts to safeguard companies from all cyber attacks.
Free Courses for You
| Course Name | Course Name |
| Django Course | Affiliate Marketing Course |
| Semrush Course | Video Editing Course |
| Blogging Course | AngularJS Course |
| Shopify Course | Photoshop Course |
Ethical Hacking Roadmap FAQs
An ethical hacking roadmap includes the following steps:
-Knowledge of computer systems and networks
-Proficiency in Programming Languages
-Networking and Security Concepts
-Web Application and Database Knowledge
-Understanding of Operating Systems
-Familiarity with Ethical hacking Tools
-Problem-solving and Analytical Thinking
-Knowledge of Common Attack Vectors and Techniques
-Certifications
An ethical hacker career doesn’t require any specific qualifications or degree. However, basic technical and programming skills will be beneficial. You can get a professional certification by joining a reliable ethical hacking course.
Various online platforms like WsCube Tech are available to help you learn ethical hacking. You can join an online ethical hacking course or training program, watch videos, or sign up for tutorials.
Yes, you need a basic programming language to be an ethical hacker because it uses Python for automation, scripting, and penetration testing. The best part is our ethical hacking course includes programming fundamentals, so beginners and learners with no technical background can learn ethical hacking.
Your ethical hacking roadmap must include tools like Burp Suite, Kali Linux, Hydra, Nmap, John the Ripper, Metasploit, and Wireshark.
You can use the given legal and safe platforms for practice:
-TryHackMe
-OverTheWire
-Hack The Box
-OWASP Juice Shop
-Capture the Flag (CTF) challenges
Industries like finance, defense, banking, IT, healthcare, and the government hire skilled, ethical hackers to secure their systems.
The duration may vary depending on your academic background, knowledge, and skills. A comprehensive ethical hacking course can be for 2-6 months, and then you need to do a 6-month internship to be proficient.
Once you complete the ethical hacking roadmap, you can apply for the following job roles:
-Penetration Tester
-Cybersecurity Consultant
-Vulnerability Assessor
-Security Analyst
-Security Architect
Linux is crucial for ethical hacking as it provides tools and a secure environment for penetration testing, network monitoring, and scripting.
Surely, if you are a beginner with zero or little experience in the technical field, you can still start a career as an ethical hacker. However, you must have basic knowledge of networking and cybersecurity fundamentals and gradually learn the advanced tools and concepts.
Due to the rise in cyberattacks and attention toward cybersecurity, companies are looking for skilled ethical hackers who can ensure data and system security.
With rising security concerns, the future of ethical hacking and ethical hackers looks promising. Advanced technologies like IoT, cloud computing, and AI will open doors to new and lucrative opportunities in cybersecurity.
As an ethical hacker, networking knowledge is crucial for you. It helps you understand the protocols like DNS, TCP/IP, and DHCP required for identifying vulnerabilities.
Apart from technical skills, ethical hackers must also possess some crucial soft skills, including attention to detail, problem-solving, critical thinking, adaptability, and communication.
Conclusion
Ethical hacking is an increasingly important field in the cybersecurity world. With the proper education, training, and certification, anyone with a passion for technology and an interest in cybersecurity can pursue a career as an ethical hacker. As the demand for skilled, ethical hackers grows, professionals must focus on upskilling and ongoing professional development to stay ahead of the curve.
However, it’s important to note that formal education is one of many ways to gain the necessary skills and knowledge to succeed in this field. Self-learning, practical experience, and participation in cybersecurity communities can also be valuable. We hope you know how to become an ethical hacker, so whether you are just starting or looking to make a career change, now is the time to focus on upskilling in this exciting and dynamic field.